WPA2-PSK vs WPA2-Enterprise: hacking and hardening
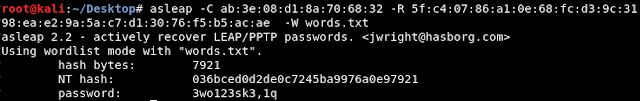
This post has the aim to summarise the security aspects of WPA2, with a focus on WPA2-Enterprise hacking. At the end, EAP-TLS is presented as a pretty secure implementation. WPA2 in brief The Wi-Fi Protected Access is a wireless technology designed to secure the communiciations between stations and the Access Point from eavesdropping and tampering attacks. It is defined in 802.11i standard and has been adopted in home, small business (WPA2-Personal) and enterprises (WPA2-Enterprise) since 2004. The WPA2 implementation is based on the 4-way handshake. The PMK (pairwise master key) is the value that both station and AP know and from which the PTK (pairwise transient key) is calculated and valid for the session. The station MAC, the AP MAC and two nonces (A-Nonce, S-Nonce) that are exchanged during the 4-way handshake are also part of the PTK generation process. From an offensive point of view, capturing the messages of the 4-way handshake that are tr...
